Creating a SAML Identity Provider using Shibboleth 3
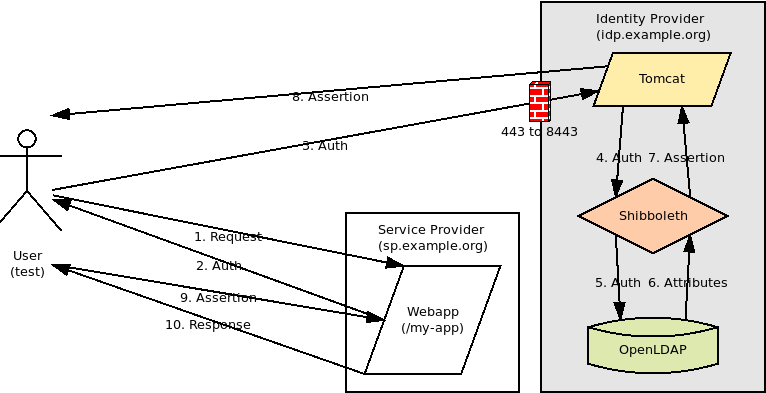
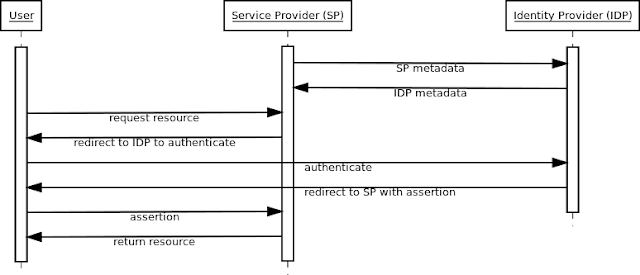
An Identity Provider (IDP) is a key component in any project using SAML authentication. It is responsible for handling Authentication Requests from Service Providers (SP), authenticating users, resolving user attributes, and creating Assertions. In this post, I will demonstrate how to install and configure a Shibboleth IDP on Ubuntu Linux using Tomcat and OpenLDAP. Identity Provider in the SAML authentication process The following settings will be used in this demo: SP entity ID: https://sp.example.org SP callback URL: https://sp.example.org/my-app/saml IDP entity ID: https://idp.example.org/idp/shibboleth Generating SP Metadata The Identity Provider requires some information about each Service Provider it is handling Authentication Requests for including its Entity ID, its signing and encryption policy, the keys used for signing/encryption (if applicable), and the callback URL where the IDP should post Assertions. In Shibboleth, this information is pr